Information Theft • Information theft occurs when someone steals personal or confidential information • Encryption is a process of converting data that i readable by humans into encoded characters to prevent unauthorized access
Information Theft • Information theft occurs when someone steals personal or confidential information • Encryption is a process of converting data that i readable by humans into encoded characters to prevent unauthorized access
Related questions
Question
Assessment 1.
ESTABLISH a SIMPLE presentation about the pictures and elaborate an explanation.

Transcribed Image Text:Information Theft
Information theft occurs when someone steals
personal or confidential information
Encryption is a process of converting data that is
readable by humans into encoded characters to
prevent unauthorized access
Page 229
Information Theft
© 2016 Cengage Learning®. May not be scanned, copied
or duplicated, or posted to a publicly accessible website,
in whole or in part.
An Example of Public Key Encryption
Step 1
The sender creates a document
to be sent via I to the receiver.
CONFIDENTIAL
The new
plant will
be located...
Step 2
The sender uses the
receiver's public key
to encrypt a message.
AA311C253
430250C
4CAD078
32EC8EF
Step 3
The receiver uses his
or her private key to
decrypt the message.
Step 4
The receiver can read or print
the decrypted message.
CONFIDENTIAL
The new
plant will
be located...
Transcribed Image Text:Information Theft
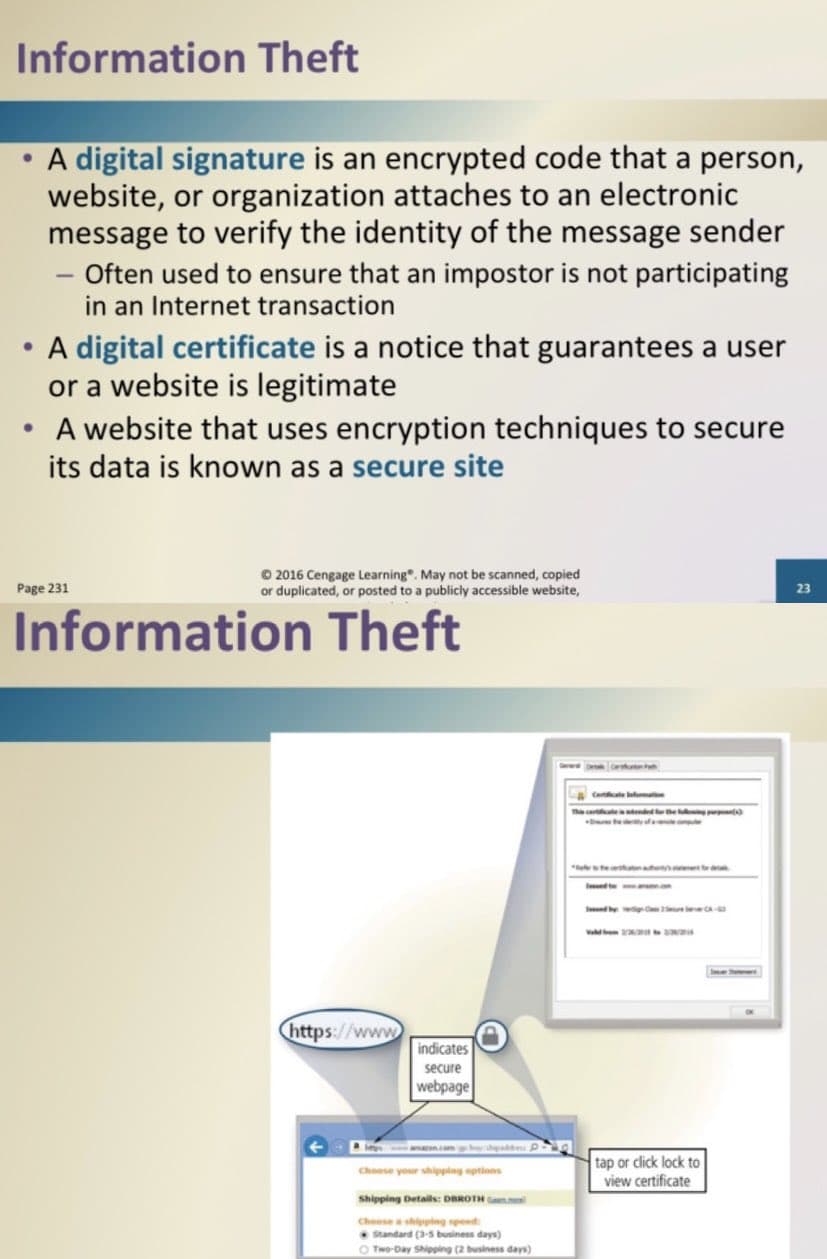
●
A digital signature is an encrypted code that a person,
website, or organization attaches to an electronic
message to verify the identity of the message sender
- Often used to ensure that an impostor is not participating
in an Internet transaction
A digital certificate is a notice that guarantees a user
or a website is legitimate
A website that uses encryption techniques to secure
its data is known as a secure site
Page 231
© 2016 Cengage Learning. May not be scanned, copied
or duplicated, or posted to a publicly accessible website,
Information Theft
https://www
indicates
secure
webpage
beton.com gabay shipaddress P
Choose your shipping options
Shipping Details: DBROTH
Choose a shipping speed:
Standard (3-5 business days)
Two-Day Shipping (2 business days)
This catended for the
tap or click lock to
view certificate
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Step 1: Information Theft and Encryption- Safeguarding Personal and Confidential Data
VIEWStep 2: Key Components of Encryption:
VIEWStep 3: Advantages of Encryption in Information Security:
VIEWStep 4: The steps involved in a basic example of public key encryption:
VIEWStep 5: Information Theft and Security Measures- Digital Signatures, Digital Certificates, and Secure Sites
VIEWStep 6: Understanding Secure Web Connections-HTTPS, Lock Icons, and Certificates
VIEWSolution
VIEWTrending now
This is a popular solution!
Step by step
Solved in 7 steps
